I don't really remember how much time people ask questions about SOCKS my whatsapp chat fulled with this type of question like hey do you know how to use socks ? i wanna card but i cant use socks... that show they haven’t taken the time to learn what it is. So i think first of all i just create a tutorial then at the end of tutorial i gave a full introduction about S0cks.
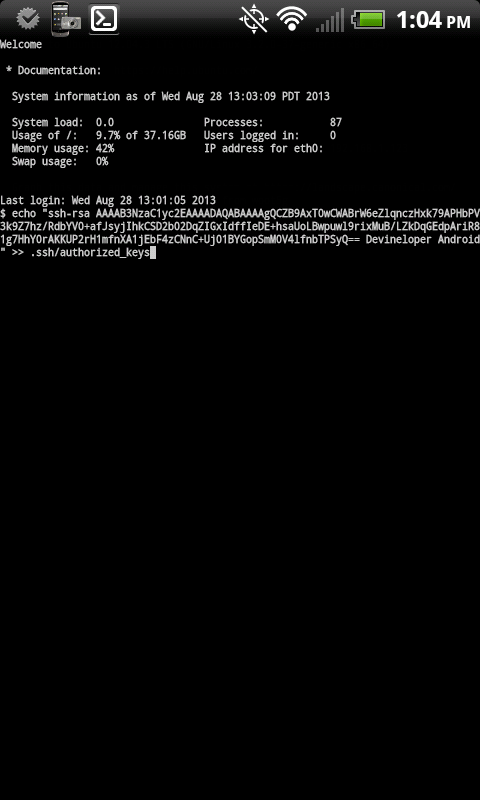
After you copy your key, type
Overview
SOCKS is a protocol that is intended to act a circuit level proxy for applications.
It is very different from ‘normal’ proxy because they are application proxies. For example, when you use a HTTP proxy you are actually forwarding the HTTP request, and the HTTP proxy server then performs the request on your behalf. An example of this would be asking someone to pass you the salt at the dinner table, who then gets the salt shaker, and passes it to you.
The SOCKS protocol is roughly equivalent to setting up an IP tunnel with a firewall and the protocol requests are then initiated from the firewall.
The client contact the SOCKS proxy server and, by exchanging messages defined by the SOCKS protocol, negotiates a proxy connection. When a connection is established, the client communicates with the SOCKS server using the SOCKS protocol. The external server communicates with the SOCKS server as if it were the actual client.
How it works
SOCKS is client/server. A users’ workstation must have a SOCKS client installed, either in the application (such as putty, Firefox), or deep in the TCP/IP stack where the client software will redirect packets into a SOCKS tunnel.
The SOCKS client will initiate a connection to a SOCKS server. The SOCKS protocol allows for authentication and logging of the connection requests.
Here is the confusing bit:
The SOCKS server then acts as the IP Client for the connection request.
This means that the external server is only aware of the SOCKS Server (the proxy).
_______________________________
search tag:
_______________________________
android ssh tunnel without root
android socks proxy no root
android chrome socks proxy
android ssh tunnel port forwarding
how to use ssh tunnel android
how to use proxydroid
juice ssh tunnel
proxy app for android without root
HOW TO USE S0CKS IN ANDROID PHONE ?
What you’ll need:
- A Linux server or desktop that you can connect to remotely using SSH
- An Android phone or tablet
Step 1: If you have a dynamic IP address for the Linux machine, first setup dynamic DNS so you can always get back to your server. Otherwise, you’ll need to write down your IP address every time you leave the house. Here’s an old Wired article that still seems relevant, though the recommended DynDNS.com is no longer “Free”.
Edit: DynDNS has axed their free service completely.
Edit: DynDNS has axed their free service completely.
Step 2: On your [Android] device, download and install ConnectBot and Firefox.
Step 3: Open ConnectBot and generate a public/private key pair. You’ll use the keys to login to your server without having to enter a password every time. To generate a key pair, hit menu and select “Manage Pubkeys”. Then hit menu again and select “Generate”. You’ll be prompted to setup your key details. The settings are up to you. If you set a password for your key pair, you’ll be prompted to enter it to unlock the key the first time you want to connect to your server. Hit “Generate” when you’re done with your settings to generate your key. You’ll be prompted with a blue box to help randomize the key. Just move your finger in a random manner in the blue box until it starts to generate your keys. Once complete, you’ll see the nickname you gave your key, along with a red lock icon.
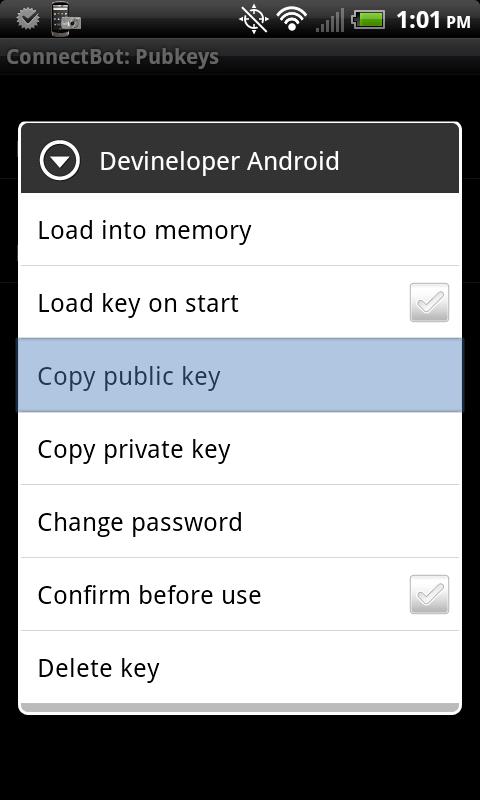
Step 4: In ConnectBot->Manage Pubkeys, long press on the key you generated in step 3 until a menu appears, then select “Copy public key” to copy the public key to memory. You’ll paste this onto your SSH server in step 6 to avoid having to enter a password. You can also optionally unlock your key here by tapping the red icon and entering your password. If you don’t, you’ll have to enter it the first time you try to connect to your server using your key.
Step 5: Create a connection to your Linux server using ConnectBot. Just enter your username@yourURL:port in the box at the bottom of the main screen and hit the enter key. Enter the password for your username when prompted and hit the enter key again to complete the connection.
Step 6: (Optional) Copy your public key to your Linux server to avoid having to enter your password in the future. After you connect in step 4, enter the following, making sure to paste the public key you copied in step 3 by hitting Menu and “Paste” (Keep the quotes shown below):

After you copy your key, type
exit or hit menu and select “Disconnect”. Then try to connect again. You shouldn’t be prompted for a password.Step 7: Hit Menu and select “Port Forwards”. Then hit Menu again and select “Add port forward”.
- Nickname: Anything you want
- Type: Dynamic (SOCKS)
- Source port: 8080 (Make sure you enter a port. The default is greyed out and just a placeholder. If you don’t enter a port, your Port Forward will disappear and you’ll be left scratching your head as to why)
- Tap “Create port forward” and make sure you see your new port forward listed. If not, double-check that you entered a port.
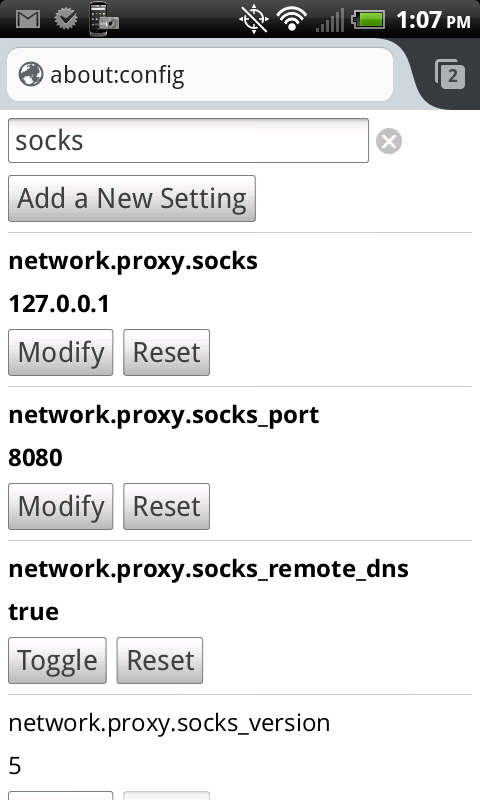
Step 8: Configure Firefox to use your newly created SSH tunnel. Open Firefox and type “about:config” in the address bar. Search for and set the following values:
- network.proxy.socks: 127.0.0.1
- network.proxy.socks_port: 8080 (or whatever port you chose in step 7)
- network.proxy.socks_remote_dns: true
- network.proxy.type: 1 (this tells Firefox to use your manual proxy settings)

Step 9: Done! There are a couple of things you can do to check if your proxy is working.
- Check your IP address
- When connected to a WiFi or mobile network that’s different from your Linux server’s network, google “what’s my ip” in Firefox and note your IP address.
- Open another browser (one that you haven’t set up to use the proxy) and do the same. The IP address in Firefox should match the IP address of your Linux server, while the IP address in the other browser should be your device’s external IP. The two IP addresses should not match.
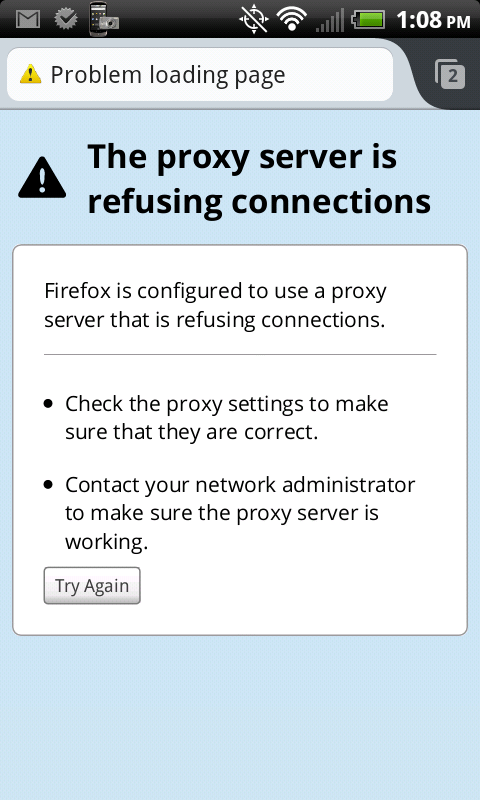
- Close the SSH tunnel and try to browse the Internet
- Open ConnectBot and disconnect the SSH tunnel by typing
exitin the shell and hitting the enter key, or by tapping menu and selecting “Disconnect”. - Open Firefox and attempt to browse the internet. You should see a proxy refused connection error.
- Open ConnectBot and disconnect the SSH tunnel by typing

Once you verify your new SOCKS proxy is working, you can be confident that your nosy fellow shoppers can’t see where you’re browsing. Unless, of course, they’re standing over your shoulder.
Overview
SOCKS is a protocol that is intended to act a circuit level proxy for applications.
It is very different from ‘normal’ proxy because they are application proxies. For example, when you use a HTTP proxy you are actually forwarding the HTTP request, and the HTTP proxy server then performs the request on your behalf. An example of this would be asking someone to pass you the salt at the dinner table, who then gets the salt shaker, and passes it to you.
The SOCKS protocol is roughly equivalent to setting up an IP tunnel with a firewall and the protocol requests are then initiated from the firewall.
The client contact the SOCKS proxy server and, by exchanging messages defined by the SOCKS protocol, negotiates a proxy connection. When a connection is established, the client communicates with the SOCKS server using the SOCKS protocol. The external server communicates with the SOCKS server as if it were the actual client.
How it works
SOCKS is client/server. A users’ workstation must have a SOCKS client installed, either in the application (such as putty, Firefox), or deep in the TCP/IP stack where the client software will redirect packets into a SOCKS tunnel.
The SOCKS client will initiate a connection to a SOCKS server. The SOCKS protocol allows for authentication and logging of the connection requests.
Here is the confusing bit:
The SOCKS server then acts as the IP Client for the connection request.
This means that the external server is only aware of the SOCKS Server (the proxy).
_______________________________
search tag:
_______________________________
android ssh tunnel without root
android socks proxy no root
android chrome socks proxy
android ssh tunnel port forwarding
how to use ssh tunnel android
how to use proxydroid
juice ssh tunnel
proxy app for android without root
How to use SOCKS in Android phone for carding ?
 Reviewed by Unknown
on
February 04, 2016
Rating:
Reviewed by Unknown
on
February 04, 2016
Rating:
 Reviewed by Unknown
on
February 04, 2016
Rating:
Reviewed by Unknown
on
February 04, 2016
Rating:















No comments: